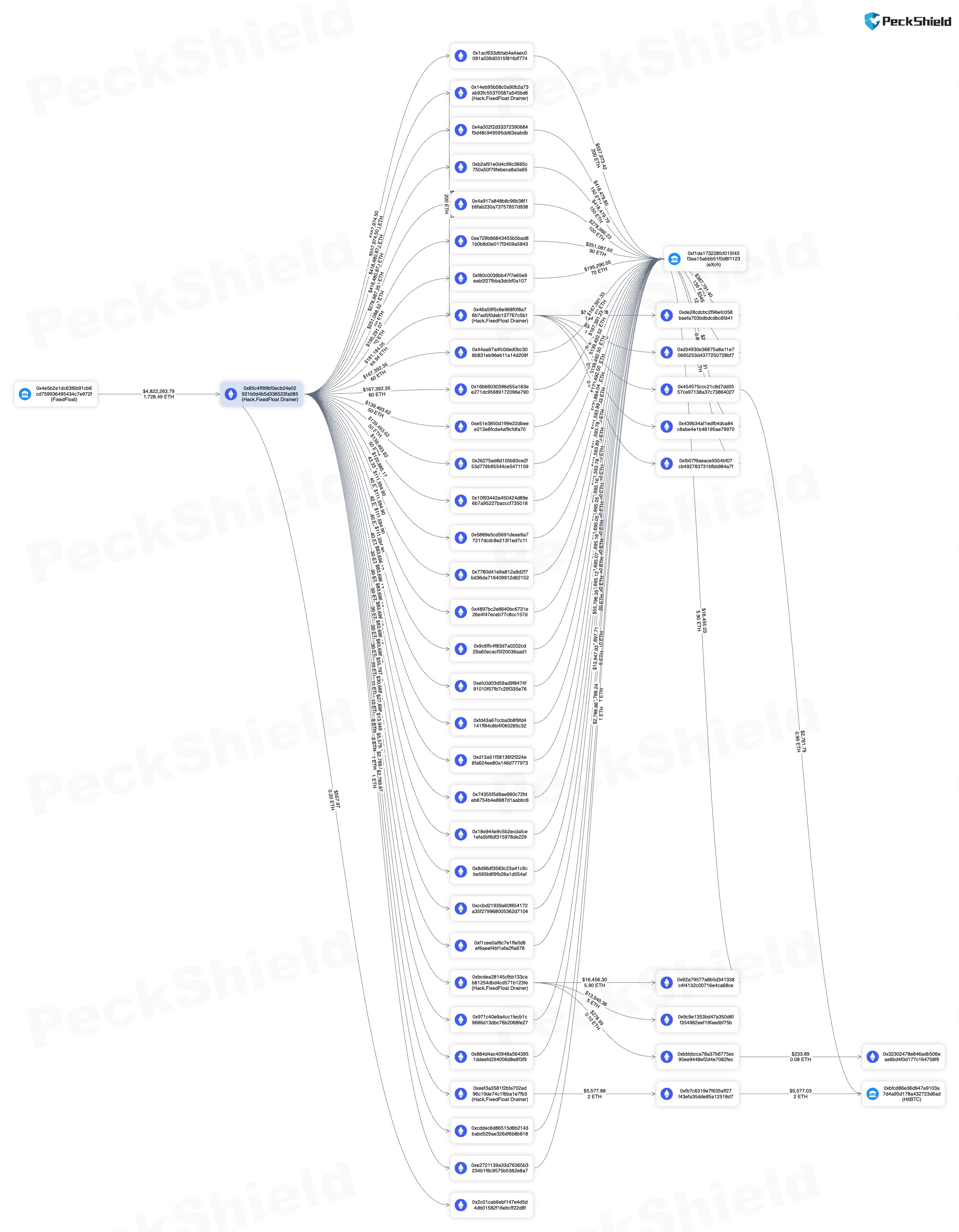
In February, the decentralized cryptocurrency exchange FixedFloat experienced a drainer attack, resulting in the loss of over $26 million worth of Bitcoin (BTC) and Ethereum (ETH). By late March, the exchange suffered a second exploit, leading to an additional loss of $2.8 million.
A few months later, FixedFloat shared the details of these incidents and ongoing investigation with BeInCrypto.
FixedFloat has been hacked twice this year. How did this happen?
The first hack occurred on the night of February 16-17. This was an external attack caused by vulnerabilities in our security structure. A hacker exploited a vulnerability in our security and was able to gain access to some of FixedFloat’s functions. The second breach took place on March 31, where the hacker exploited a vulnerability in a third-party service we were using at the time.
Was the second hack committed by the same hacker who committed the previous hack, or was it a different attacker?
We believe the same hacker committed both hacks because the attacks originated from the same IP address. We cannot provide all the details at the moment. However, we can report that hackers possess a large number of compromised servers.
On some of these servers, they have deployed the infrastructure for attacks. They likely did not store evidence on their own devices, instead using third-party servers. The hackers utilized numerous unique IP addresses; however, some were used to launch both attacks.
Do you have information about who exactly is behind the hacks?
We have been using Time4VPS hosting for a long time. This is a fairly large web hosting provider in Europe, operating since 2012. We chose Time4VPS for our purposes, since this hosting offers fairly cheap servers with low performance. This was a convenient and profitable option for implementing some technical solutions at the initial stage of development of our project.
Over the past years, we have migrated our subservers and wallets. At the beginning of 2024, several low-power nodes with wallets and some subsystems remained on the Time4VPS server. After the first hack, the hacker discovered the IP address of one of our technical servers rented from Time4VPS.
How did the hacker use the information?
The hacker logged into all our servers, rented from Time4VPS hosting, simultaneously, despite knowing only one IP address. We immediately changed all passwords on servers and accounts, but the hacker quickly changed the passwords again. We found a solution to prevent server authorization and started transitioning from this hosting provider.
However, the hacker gained access to all hoster functions, including global access to all servers, rendering our solutions ineffective. The hacker changed the account email to an invalid one, preventing us from logging in or receiving password change notifications. They connected to the servers without authorization.
At this point, we realized the need to destroy the servers and remove them from the whitelists immediately. Our delay in doing so allowed the hacker to send requests that enabled them to steal funds.
Have you contacted Time4VPS support?
On March 31, immediately after discovering unauthorized access to our servers, we contacted Time4VPS to report the hack. We were extremely surprised by their inaction. Technical support informed us that the technicians had the day off and could not assist us. The following day, the Time4VPS team remained inactive. They merely advised us to change the passwords on our account.
We eventually convinced them to verify that certain actions could not be performed through their personal account. Only then did they confirm the hack and promise to provide a report on the incident the next day.
Have you received a hack report from Time4VPS?
More than three months have passed, and there is still no report from Time4VPS. Instead, they requested that we provide some documents through their system. We refused because Time4VPS representatives have not confirmed that they found and fixed the vulnerability. Their demands have created the risk of another information leak.
We agreed to cooperate only with the direct involvement of law enforcement or after they confirmed the vulnerability had been corrected. Additionally, our lawyer was prepared to provide the necessary documents directly at the company’s office to receive reports and assistance. However, Time4VPS management rejected this offer.
Why do you think Time4VPS was inactive at the time of the hack and did not provide assistance after it?
We do not exclude the possibility that a hoster’s employee could have facilitated the hacking. However, we are more inclined to believe that Time4VPS and the Lithuanian company behind it are simply careless. We believe the hoster’s critical vulnerabilities remain unfixed, leaving all their clients’ data unprotected from hacker attacks.
Did the hack impact your customers?
This incident caused problems not only for us but also for our users. As soon as we detected the hack, we turned off FixedFloat and suspended all ongoing exchanges.
FixedFloat is an automated, non-custodial, decentralized cryptocurrency exchange service, so we don’t store our users’ funds. Additionally, FixedFloat is not a cryptocurrency mixer. We send funds to exchanges only from our addresses, and this information is public.
Due to the hack, we had obligations to clients who made exchanges at that time. We have since fulfilled all obligations to our users, and completed all orders that stopped due to the service outage. Only our service suffered from the hacking and theft of funds.
What measures did you take after the hack?
The first breach was due to a security vulnerability, which we have since fixed. Unfortunately, we did not anticipate an attack from third parties. Following the second hack, our service was under maintenance for over two months. During this period, our specialists worked extensively to enhance our infrastructure and protect against such attacks.
We have radically revised our security system. This included conducting a comprehensive audit, implementing additional security measures, and improving our threat detection and prevention systems.
Have you completed the technical work?
Yes, FixedFloat has resumed operations. Most cryptocurrencies are already available for exchange, and our specialists are working on adding new currencies. We have been providing high-quality, convenient, and fast cryptocurrency exchange services for six years, and we intend to continue our work.
From a hack survivor perspective, can you give a few recommendations to other platforms and its users on how to increase security?
As a service that has experienced two hacks for different reasons, we’d recommend the following:
- Conduct frequent audits of your security systems. Identify and address all vulnerabilities promptly.
- Plan for Provider Vulnerabilities. The second hack exploited a vulnerability in our hosting provider, Time4VPS. Platforms should anticipate such scenarios and have a robust procedure for dealing with service provider hacks.
- Always prioritize user safety. Implement strict security measures and protocols to protect user data and funds.
What steps are you taking to regain the trust of your users following these accidents?
We are actively engaging with our users through various communication channels, including social networks and forums. This allows us to inform them about the changes we have made. Currently, not all users are aware that FixedFloat has resumed operations, but we are working to spread this information.
We understand that many were concerned about the hack’s impact on our users. However, we emphasize that we are a non-custodial service and do not store user funds. Orders that were not fulfilled due to the emergency shutdown have been completed. At present, we have no financial obligations to our users.
Trusted
Disclaimer
In compliance with the Trust Project guidelines, this opinion article presents the author’s perspective and may not necessarily reflect the views of BeInCrypto. BeInCrypto remains committed to transparent reporting and upholding the highest standards of journalism. Readers are advised to verify information independently and consult with a professional before making decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.


